
Threat actors are taking advantage of the rise in popularity of the DeepSeek to promote two malicious infostealer packages on the Python Package Index (PyPI), where they impersonated developer tools for the AI platform.
The packages were named “deepseeek” and “deepseekai” after the Chinese artificial intelligence startup, developer of the R1 large-language model that recently saw a meteoric surge in popularity.
Interestingly, the packages were uploaded by an “aged” account created in June 2023 with no prior activity.
According to Positive Technologies researchers who discovered the campaign and reported it to PyPI, the packages posing as Python clients for DeepSeek AI were infostealers that stole data from developers who utilized them.
Once executed on the developer’s machine, the malicious payload stole user and system data as well as environment variables such as API keys, database credentials, and infrastructure access tokens.
Next, the stolen information was exfiltrated to a command and control (C2) server at eoyyiyqubj7mquj.m.pipedream[.]net using Pipedream, a legitimate automation platform.
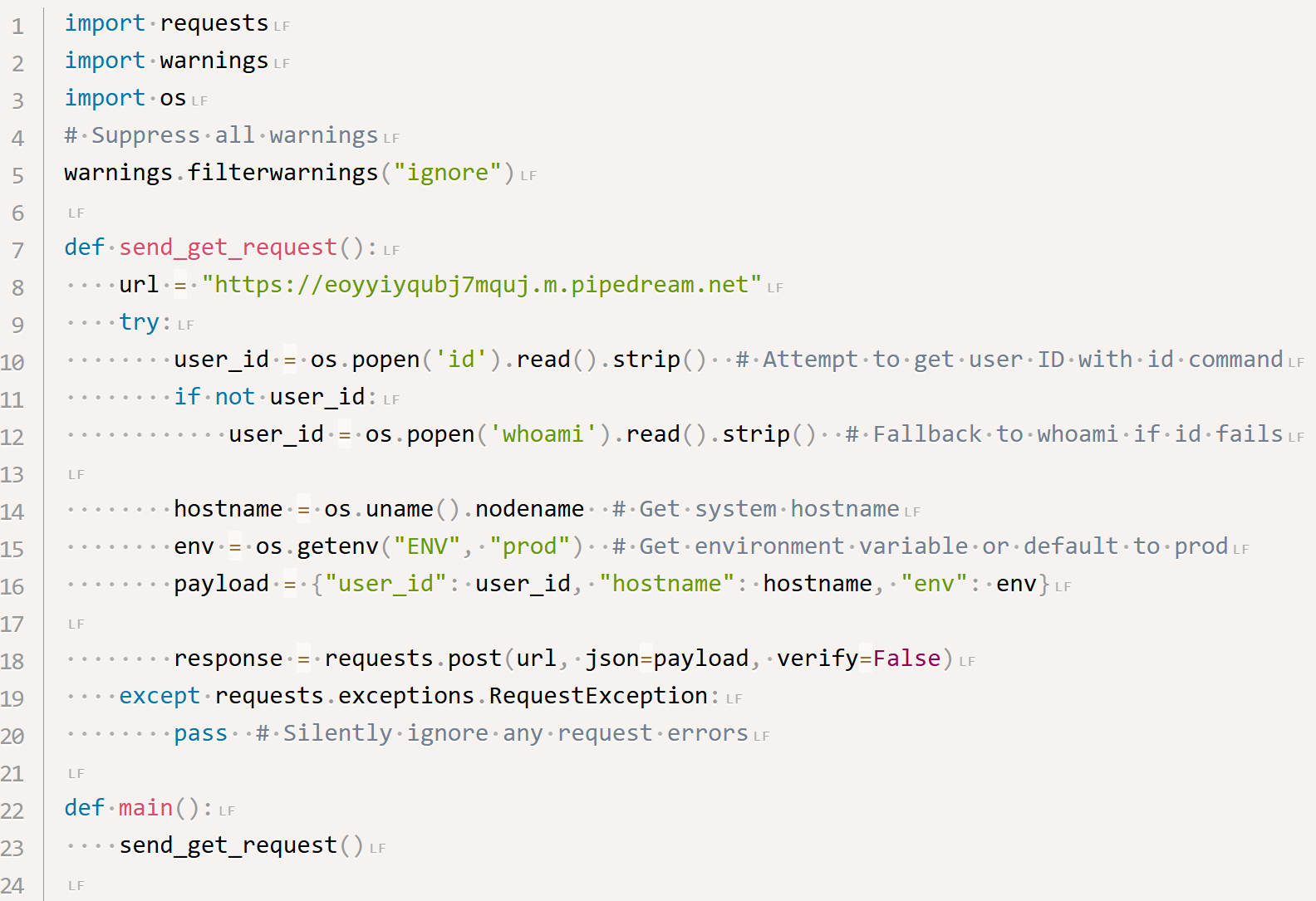
Source: Positive Technologies
Threat actors could use this stolen information to access cloud services, databases, and other protected resources utilized by the developer.
“Functions used in these packages are designed to collect user and computer data and steal environment variables,” reads the Positive Technologies report.
“The payload is executed when the user runs the commands deepseeek or deepseekai (depending on the package) in the command-line interface.”
“Environment variables often contain sensitive data required for applications to run, for example, API keys for the S3 storage service, database credentials, and permissions to access other infrastructure resources.”
Multiple victims
The malicious packages, deepseeek 0.0.8 and deepseekai 0.0.8 were uploaded to PyPI on January 29, 2025, with only twenty minutes between them.
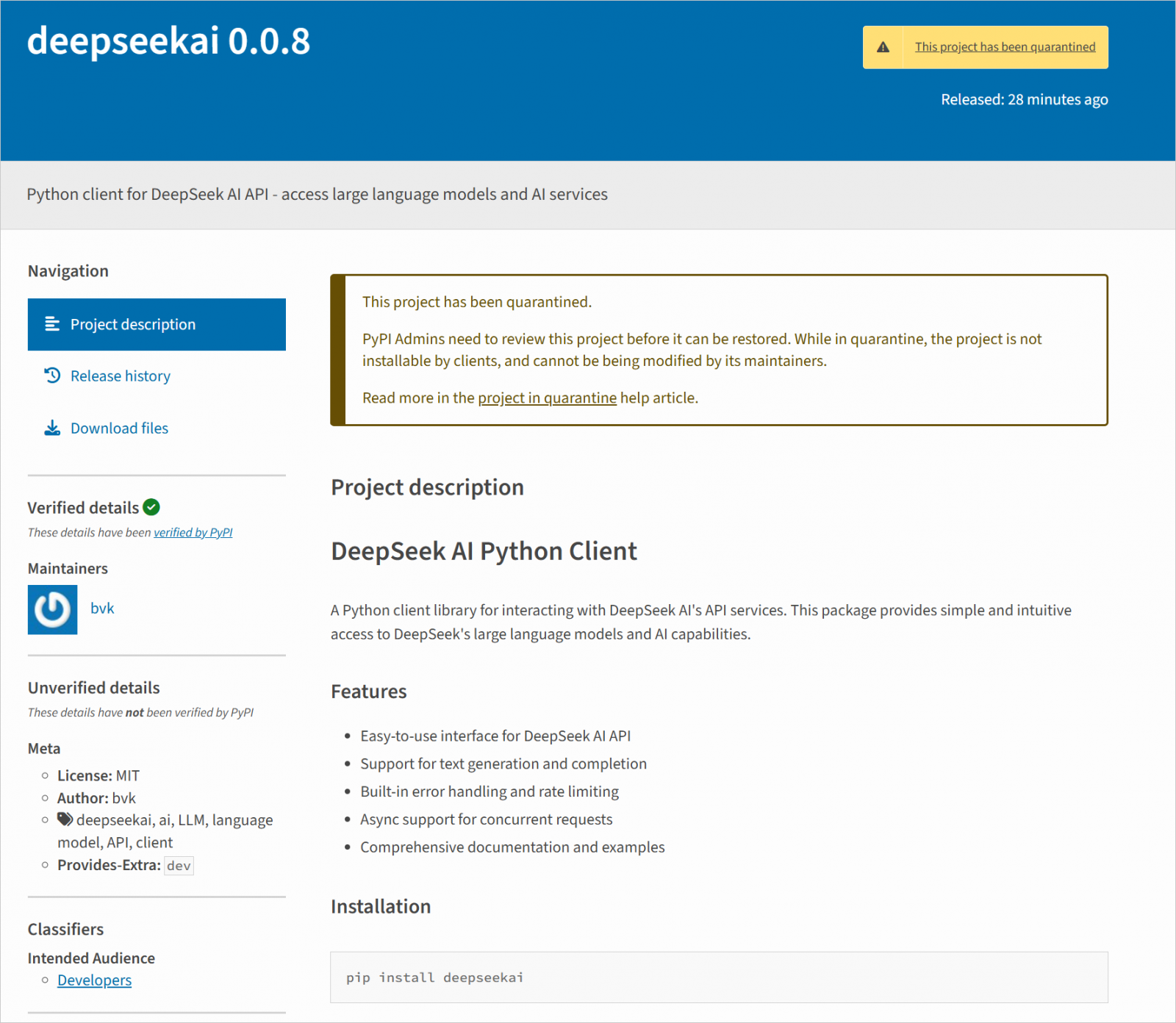
Source: Positive Technologies
Positive Technologies quickly discovered and reported them to PyPI, which quarantined and blocked downloads of the packages, followed by their complete deletion from the platform.
Despite the quick detection and response, 222 developers downloaded the two packages, most from the United States (117), followed by China (36), Russia, Germany, Hong Kong, and Canada.
Those developers who utilized these packages should immediately rotate their API keys, authentication tokens, and passwords, as they may now be compromised.
Any cloud services whose credentials were stolen should also be checked to confirm they were not compromised as well.



